- cross-posted to:
- lgbtq_plus@lemmy.blahaj.zone
- transgender@lemmy.ml
- cross-posted to:
- lgbtq_plus@lemmy.blahaj.zone
- transgender@lemmy.ml
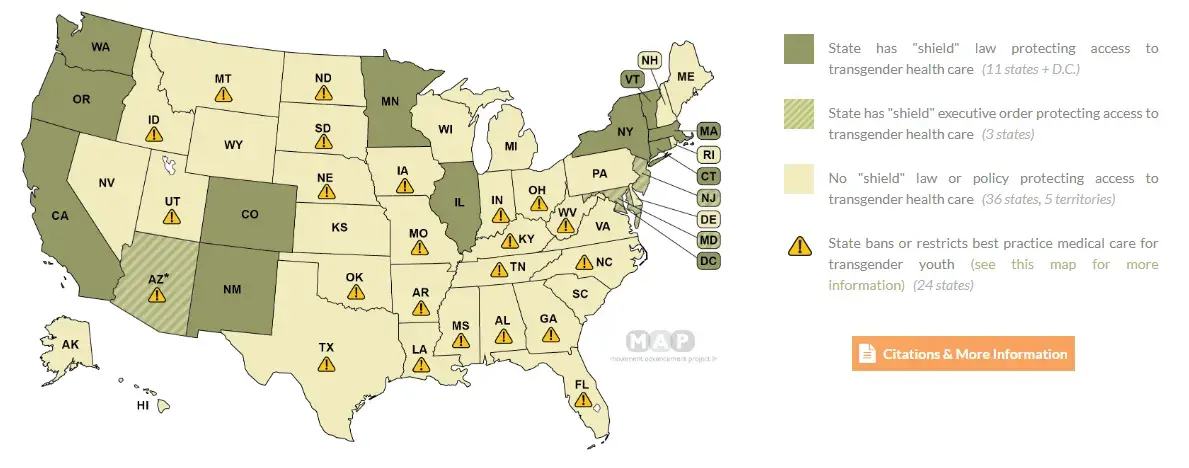

Tennessee has recently passed a bill, effective July 1st 2024, declaring it a class-C felony to “recruit, harbor, or transport an unemancipated minor within this state” for transgender healthcare procedures, carrying a sentence of 3-15 years in prison. This applies over state lines and states that do not have anti-extradition laws relating to trans rights can extradite you to Tennessee.
Notably: the bill is vague. This means: telling stories of your own transition, describing your healthcare experiences to an open group chat, describing your trans experiences on a public website, creating trans health guides online, describing how you have gotten DIY HRT, describing anything to do with trans healthcare, even as a cis person, can result in a class-C felony conviction.
Given that being arrested in any capacity for transgender people can be an incredibly dangerous experience (CW: SV), I strongly suggest you begin caring about opsec, stop referring to where you live, use VPNs, stop using apps like Discord, and stop using social media sites that track your IP or user agent fingerprint while unprotected. Remember that for a bill like this to be challenged in court, you have to be arrested first.
Will discuss creating / linking to a transgender matrix chat so that we can help people to move off of things like discord.



For one-to-one comms Signal is easier to get started with. Matrix requires a hosting service (or just reliance on the main matrix.org instance), or trust in a server administrator to run one. But it is good software. But unfortunately for group chat it’s not as easy to get started as Discord, due to the encrypted nature of Matrix. But Discord shouldn’t be considered secure or private, not really. It’s just more proprietary spyware, at the end of the day.
Certainly, no matter what, no SMS.
Didn’t Signal recently get outed as having a back door?
Honestly, as long as you’re using a phone, you’re at risk. As LLMs becomes more portable it’s just a matter of time before our own phones will narc on us. Most of them already have some sort of ocr /image describer process happening on our photo rolls.
I think that’s where threat modeling comes in. Unfortunately, if you’re threat modeling against the US government, you’re mostly relying on the laziness and ineptitude of some random LEO to not follow through on looking into you further. You can absolutely make things better, but if you get a target on your back you’re fucked. There’s a reason Snowden’s in Russia.
Signal is incredibly dangerous, it’s a US hosted and domiciled company, and they have a legal obligation to forward anything they know about you to the federal government if asked.
I wouldn’t knock it until I learn of a situation where Signal handed data over to the government that wasn’t encrypted mishmash or derived from side-channel that wasn’t specifically related to Signal (the app or the protocol) itself. I do fully agree, however, that a phone number as a registration ID is bad.
But as it stands I don’t consider the point that it’s located in the USA to be fully incriminating. Just as I don’t find it a problem that Matrix and Vector Creations were an offshoot from an Israeli tech company*. The protocol, and how it functions, are what matters.
*And yes, the major caveat here is that you can inspect and run the Matrix server code (Synapse or Dendrite), but not the Signal server code.
Read the section on NSL’s (national security letters) in the link above. Any US domiciled company must give up it’s data when asked, and it’s illegal for them to tell their users they were forced to do so. The Obama regime admitted to issuing 60 of these every single day, there’s no way Signal isn’t compromised.
Matrix doesn’t need to be hosted in the US, so they don’t have that problem. Using any US-hosted service is a big no-no.